Ophcrack Mirror
Ophcrack (no tables) Ophcrack XP (Password Finder) Ophcrack Vista/7 (Password Finder) Parted Magic (Partition Tools) PING (Partimg Is Not Ghost). ⇒ 5.4MB YUMI UEFI 0.0.2.9 Mirror. Last Updated on November 17, 2020 by Pirate4All. ATTENTION: Semua links download boleh ditukar ganti. Ophcrack LiveCD is a specialist SliTaz-based live CD containing Ophcrack, an open source Windows password cracker that uses rainbow tables. The graphical program included on the live CD is reputed for being able to crack alphanumeric Windows passwords of up to 14 characters in usually just a few seconds. Visitor rating: No visitor rating given yet.
Hash Suite by Alain Espinosa
Windows XP to 10 (32- and 64-bit), shareware, free or $39.95+
Hash Suite is a very efficient auditing tool for Windows password hashes(LM, NTLM, and Domain Cached Credentials also known as DCC and DCC2).It is very fast, yet it has modest memory requirements even when attacking amillion of hashes at once.The GUI is simple, yet uses modern features offered by Windows 7 and above.Besides the password security auditing program itself, there's an includedreports engine that generates reports in multiple formats, including PDF.(The reports engine requires free Java VM from Oracle to be installed.)
pwdump byJeremy Allison
Windows NT, free (permissive BSD and GPL-compatible Open Source license)
Download local copy of pwdump (49 KB)
This handy utility dumps the password database of an NT machine thatis held in the NT registry (underHKEY_LOCAL_MACHINESECURITYSAMDomainsAccountUsers) into a validsmbpasswd format file (which is understood by practically allWindows password security auditing tools).
This is the original pwdump program.It is mostly of historical value these days.You will likely want to use a newer reimplementation such aspwdump6 instead.You might also be interested in ourfile archive with local copies of many pwdump-like and pwdump-related programs.
pwdump2 by Todd Sabin of Bindview
Windows NT/2000,free(GPL v2)
Download local copy of pwdump2 (46 KB)
This is an application which dumps the password hashes from NT's SAM database, whether or not SYSKEY is enabled on the system. NT Administrators can now enjoy the additional protection of SYSKEY, while still being able to check for weak users' passwords. The output follows the same format as the original pwdump (by Jeremy Allison) and can be used as input to password crackers. You need the SeDebugPrivilege for it to work. By default, only Administrators have this right, so this program does not compromise NT security.
pwdump3 and pwdump3eby Phil Staubs and Erik Hjelmstad of PoliVec, Inc.
Windows NT/2000,free(GPL v2)
Download local copies ofpwdump3 version 2 (87 KB) andpwdump3e (217 KB)
pwdump3 enhances the existing pwdump and pwdump2 programs developed by Jeremy Allison and Todd Sabin, respectively. pwdump3 works across the network and whether or not SYSKEY is enabled. Like the previous pwdump utilities, pwdump3 does not represent a new exploit since administrative privileges are still required on the remote system. One of the largest improvements with pwdump3 over pwdump2 is that it allows network administrators to retrieve hashes from a remote NT system.
pwdump3e provides enhanced protection of the password hash information by encrypting the data before it is passed across the network. It uses Diffie-Hellman key agreement to generate a shared key that is not passed across the network, and employs the Windows Crypto API to protect the hashes.
pwdump4 by bingle
Windows NT/2000,free(GPL v2)
Download local copy of pwdump4 (72 KB)
pwdump4 is an attempt to improve upon pwdump3.It might work in cases when pwdump3 fails (and vice versa).
pwdump5 by AntonYo!
Windows NT/2000/XP/2003, free
Download local copy of pwdump5 (28 KB)
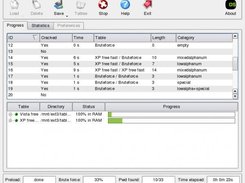
pwdump5 is an application that dumps password hashes from the SAM databaseeven if SYSKEY is enabled on the system.If SYSKEY is enabled, the program retrieves the 128-bit encryption key,which is used to encrypt/decrypt the password hashes.
pwdump6by fizzgig
Windows 2000/XP/2003/Vista,free(GPL v2)
Download local copy of pwdump6 1.7.2 inZIP (1268 KB) ortar.bz2 format (1103 KB)
pwdump6 is a significantly modified version of pwdump3e. This program is able to extract NTLM and LanMan hashes from a Windows target, regardless of whether SYSKEY is enabled. It is also capable of displaying password histories if they are available. Currently, data transfer between the client and target is NOT encrypted, so use this at your own risk if you feel eavesdropping may be a problem.
pwdump7by Andres Tarasco Acuna
Windows NT family (up through XP or Vista?), free
Download local copy of pwdump7 revision 7.1 (505 KB)
pwdump7 works with its own filesytem driver (from rkdetector.com technology) so users with administrative privileges are able to dump directly from disk both SYSTEM and SAM registry hives.Once dumped, the SYSKEY key will be retrieved from the SYSTEM hive and then used to decrypt both LanMan and NTLM hashes and dump them in pwdump like format.
Quarks PwDump originally bySebastien Kaczmarek of Quarkslab
Windows XP/2003/Vista/7/2008/8,free(GPL v3)
Original source code on GitHub (no pre-compiled binary, outdated) by Quarkslab
Revised source code on GitHub (with pre-compiled binary in Releases) by red canari
Download local copy of Quarks PwDump 0.3a by red canari (369 KB) orits source code (5.6 MB including a prerequisite library)
Quarks PwDump extracts local accounts NT/LM hashes + history, domain accounts NT/LM hashes + history, cached domain password, Bitlocker recovery information (recovery passwords & key packages). It requires administrator privileges.
pwdump8 by Fulvio Zanetti and Andrea Petralia of blackMath.it
Windows 2000/XP/Vista/7/2008/8/8.1/10/2012/2016/2019, free
Download local copy of pwdump8 8.2 (529 KB)
pwdump8 supports AES-128 encrypted hashes and thus works on Windows 10 v1607 and later, where the previous pwdump tools fail.pwdump8 works with the local Windows system, as well as with dumped SAM and SECURITY reg hives.Version 8.2 adds support for domain cached account.pwdump8 requires administrative privileges, just like the previous tools did.
Ophcrack Download Mirror
mimikatz byBenjamin DELPY `gentilkiwi`
Windows (up to latest builds of Windows 10), free (CC BY 4.0)
Ophcrack Mirror App
mimikatz is a well-known advanced tool to extract plaintexts passwords, hash, PIN code, and Kerberos tickets from memory.mimikatz can also perform pass-the-hash, pass-the-ticket, or build Golden tickets.mimikatz is an actively maintained Open Source project.
Offline NT Password & Registry Editor by Petter Nordahl-Hagen
Windows NT to 8.1 (32- and 64-bit), freeware
This is an utility (available in the form of bootable floppy and CD images) to reset the password of any user that has a valid (local) account on your NT system, by modifying the password hash in the registry's SAM file.You do not need to know the old password to set a new one.
The editor works offline, that is, you have to shutdown your computer and boot off a floppy disk or a CD. The boot disks use Linux as the OS and include stuff to access NTFS partitions and scripts to glue the whole thing together.
This will also work with SYSKEY, including the option to turn it off.
UNetbootin allows you to create bootable Live USB drives for Ubuntu and other Linux distributions without burning a CD.
You can either let UNetbootin download one of the many distributions supported out-of-the-box for you, or supply your own Linux .iso file.
Features
UNetbootin can create a bootable Live USB drive
It loads distributions either by downloading a ISO (CD image) files for you, or by using an ISO file you've already downloaded.
Using UNetbootin
Select an ISO file or a distribution to download, select a target drive (USB Drive or Hard Disk), then reboot once done. If your USB drive doesn't show up, reformat it as FAT32.
If you used the 'USB Drive' install mode: After rebooting, boot from the USB drive. On PCs, this usually involves pressing a button such as Esc or F12 immediately after you turn on your computer, while on Macs, you should hold the Option key before OSX boots.
If you used the 'Hard Disk' install mode: After rebooting, select the UNetbootin entry from the Windows Boot Menu.
Supported Distributions
UNetbootin has built-in support for automatically downloading and loading the following distributions, though installing other distributions is also supported:
UNetbootin can also be used to load various system utilities, including:
Installing Other Distributions Using UNetbootin
Download and run UNetbootin, then select the 'disk image' option and supply it with an ISO (CD image).
UNetbootin doesn't use distribution-specific rules for making your live USB drive, so most Linux ISO files should load correctly using this option. However, not all distributions support booting from USB, and some others require extra boot options or other modifications before they can boot from USB drives, so these ISO files will not work as-is. Also, ISO files for non-Linux operating systems have a different boot mechanism, so don't expect them to work either.
FAQs
Distribution X isn't on the list of supported distributions, will it work?
» Maybe, see Installing Other Distributions Using UNetbootin.
UNetbootin isn't able to download the distribution, what should I do?
Download the ISO straight from the website, then provide it to UNetbootin via the diskimage option.
My USB stick isn't booting, what should I do?
Reformat the USB drive as FAT32, then use UNetbootin again to put your distribution on the USB stick.
My USB stick/hard drive isn't detected, what should I do?
Reformat the USB drive as FAT32, then use UNetbootin again. If it still isn't showing up, use the targetdrive command line option.
How do I use UNetbootin from the command line?
» See UNetbootin Command Line Options.
How does UNetbootin work, and what does it do?
» See How UNetbootin Works.
» See USB Drive and Hard Disk Install Modes.
Where can I report bugs, submit patches, etc?
First, make sure you are using the latest version available on this website.
» See Github Issues to file a bug report.
» See Github Pull Requests to submit a patch.
Does UNetbootin have any spyware, viruses, trojans, or other malware?
No; though some anti-virus products may raise 'Trojan.generic' warnings due to the auto-uninstall feature, these are false positives. Just make sure you obtain UNetbootin from this site, not some shady third-party source. If you're absolutely paranoid, you can check the source code and compile it yourself.
What translations are available, and how can I use them?
A number of translations are included in the latest UNetbootin release. See the Translations Page for the status of each.
If a translation corresponding to your system's native language has already been included into UNetbootin, it should automatically load the corresponding translation. Alternatively, you can force the language to use via the lang=es command-line option, where you substitute es with the the 2-letter ISO 639-1 code for your language.
Can I help translate?
If you'd like to help translate this website, join the project on Transifex, then edit translations either on this website or on Transifex.
If you'd like to help translate the UNetbootin program itself, please use Launchpad Translations. If you are new to Launchpad, you will first have to join the corresponding Ubuntu Translators group for the language you intend to translate. For information on using the Launchpad Translations system, see the translations help page.
» See UNetbootin Translations
Removal Instructions (Applicable only to Hard Disk installs)
If using Windows, UNetbootin should prompt you to remove it the next time you boot into Windows. Alternatively, you can remove it via Add/Remove Programs in the Control Panel.
Ophcrack Mirrored
If using Linux, re-run the UNetbootin executable (with root priveledges), and press OK when prompted to uninstall.
Removal is only required if you used the 'Hard Drive' installation mode; to remove the bootloader from a USB drive, back up its contents and reformat it.
Uninstalling UNetbootin simply removes the UNetbootin entry from your boot menu; if you installed an operating system to a partition using UNetbootin, removing UNetbootin will not remove the OS.
To manually remove a Linux installation, you will have to restore the Windows bootloader using 'fixmbr' from a recovery CD, and use Parted Magic to delete the Linux partition and expand the Windows partition.
Where's the source code, and how can I compile or modify it?
Source code is on Github, though you may prefer a tarball of the latest release.
Ophcrack Mirrors
» See Compiling UNetbootin.
» See UNetbootin Command Line Options.
» See Building a UNetbootin Plugin.
» See Using a UNetbootin Plugin.
» See Building a Custom UNetbootin Version.
Ophcrack Mirroring
» See List of Custom UNetbootin Versions and Plugins.
License
UNetbootin was created and written by Geza Kovacs (Github: gkovacs, Launchpad: gezakovacs, contact info).
Translators are listed on the translations page.
UNetbootin is licensed under the GNU General Public License (GPL) Version 2 or above. Site materials, documentation, screenshots, and logos are licensed as Creative Commons Attribution-Share-Alike 3.0.